With securityprogram.io (SPIO), startups and SMBs can easily build a standards and audit ready security program that will gain confidence from your customers, prospects, partners, and investors.


securityprogram.io (SPIO) is a cloud-based application built to help growing companies develop a security program that meets their needs and budget.
Implementing a security program impacts all parts of a business with many tasks to be handle by a number of staff. SPIO helps guide you through the process so you easily manage all components in one central location.
With SPIO, you can confidently demonstrate your security posture to all stakeholders.
You're already sprinting. Leverage a tool and a team that can keep pace with you.
Document templates and built-in training allow you to make pragmatic improvements that improve security and demonstrate alignment to standards that customers trust.
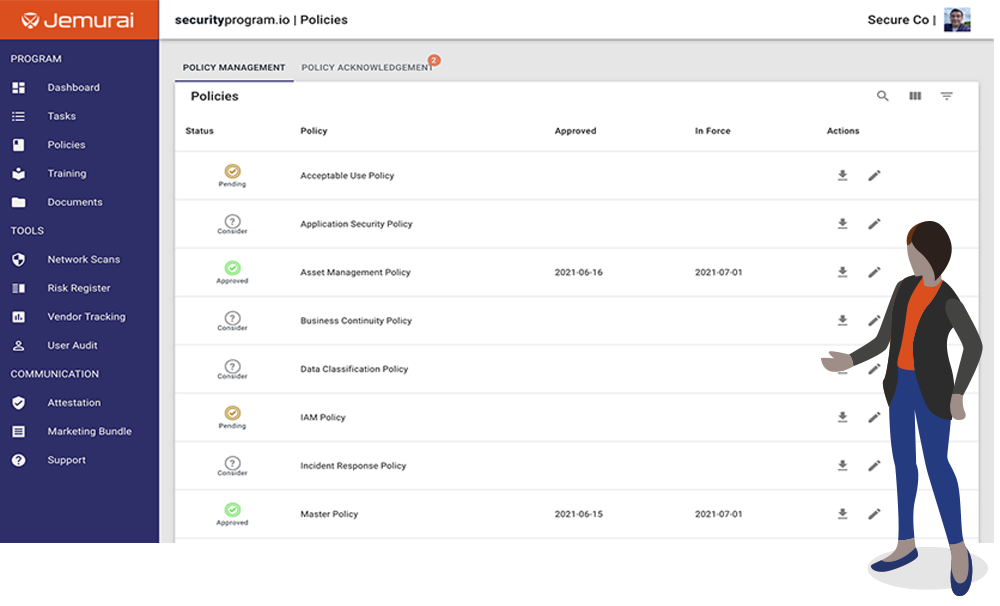
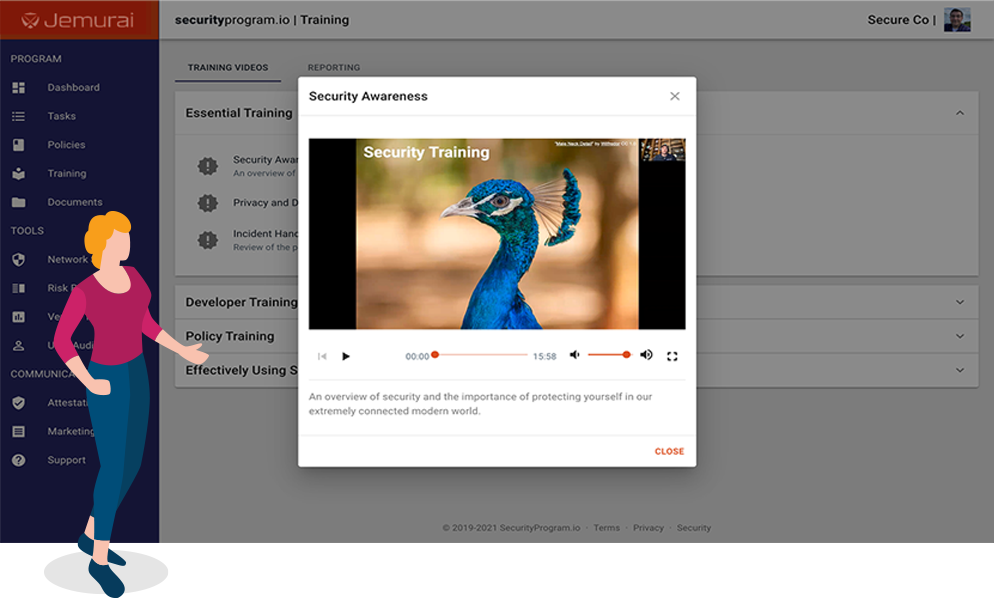
Training conducted by industry experts is a cornerstone of our security program. To secure a business, employees should go through security training that is easy to understand and implement.
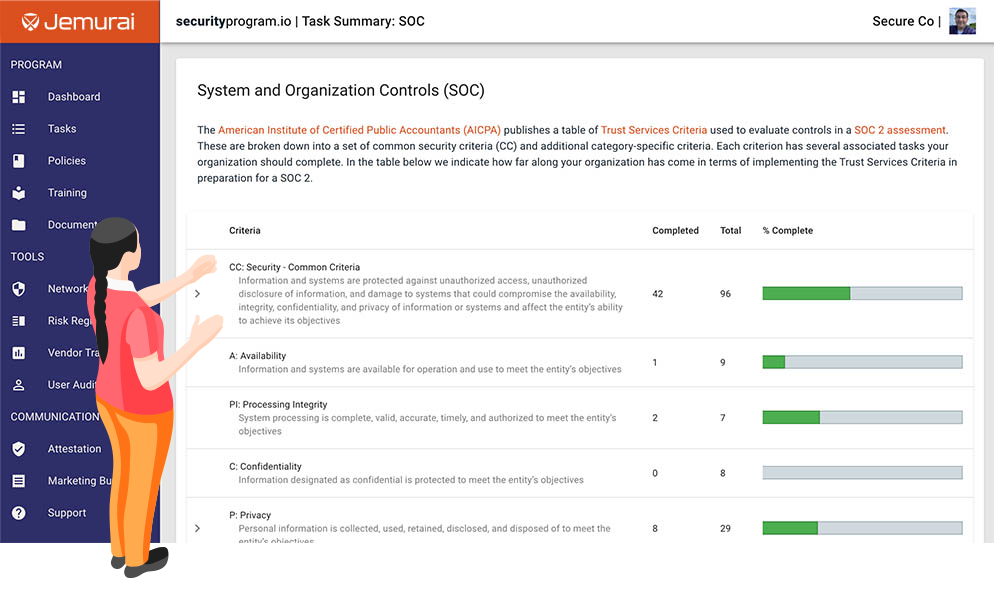
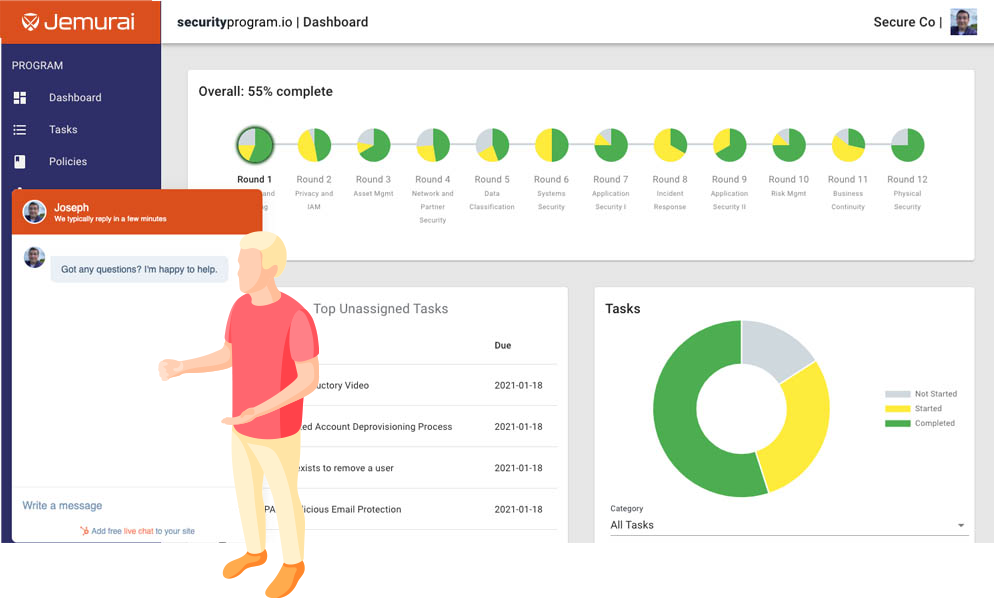
Not just progress, but detailed progress related to common standards. Our dashboard captures a deep view of your security journey that can be an effective communication tool for all stakeholders.
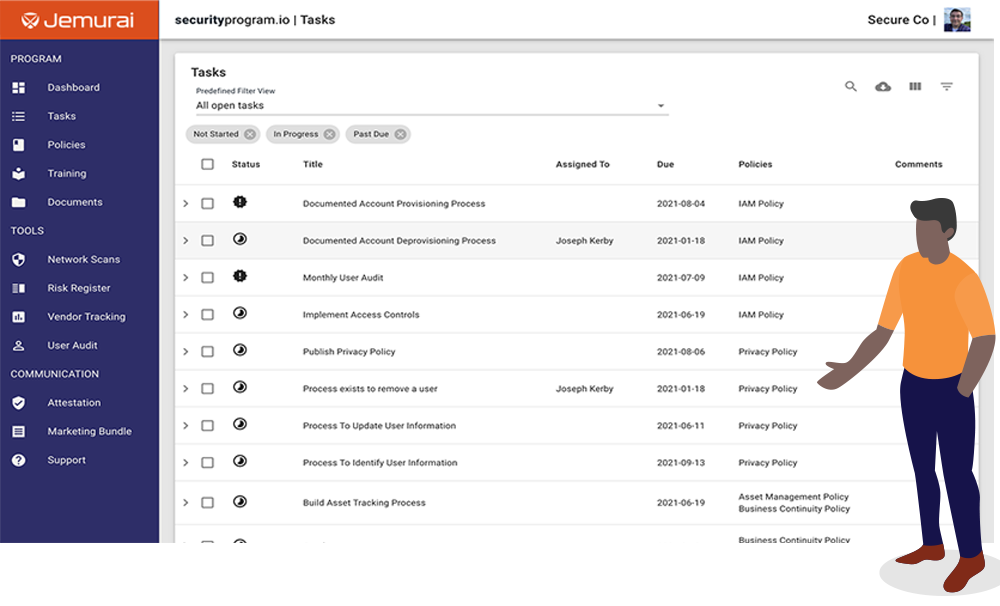
Securing a business takes a lot of work across many departments. Manage all this work in one central place where you can assign tasks, set due dates, keep running notes and attach evidence.

Security can be hard, we are here to help make it easy! Support is available through the app, Slack, email, and team based support if you ever run into problems.
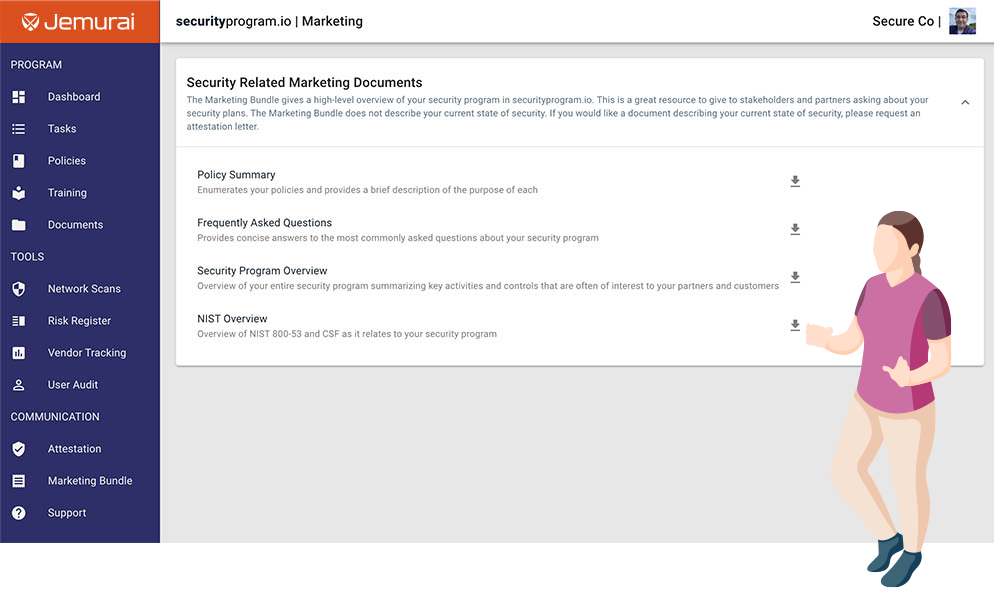
Documentation to market the security work you are doing. These packets make it easy to communicate with customers about your security program.
securityprogram.io will help you build a cybersecurity program that you can confidently share with your customers, investors, and regulators.
Our easy-to-use app enables you to:
